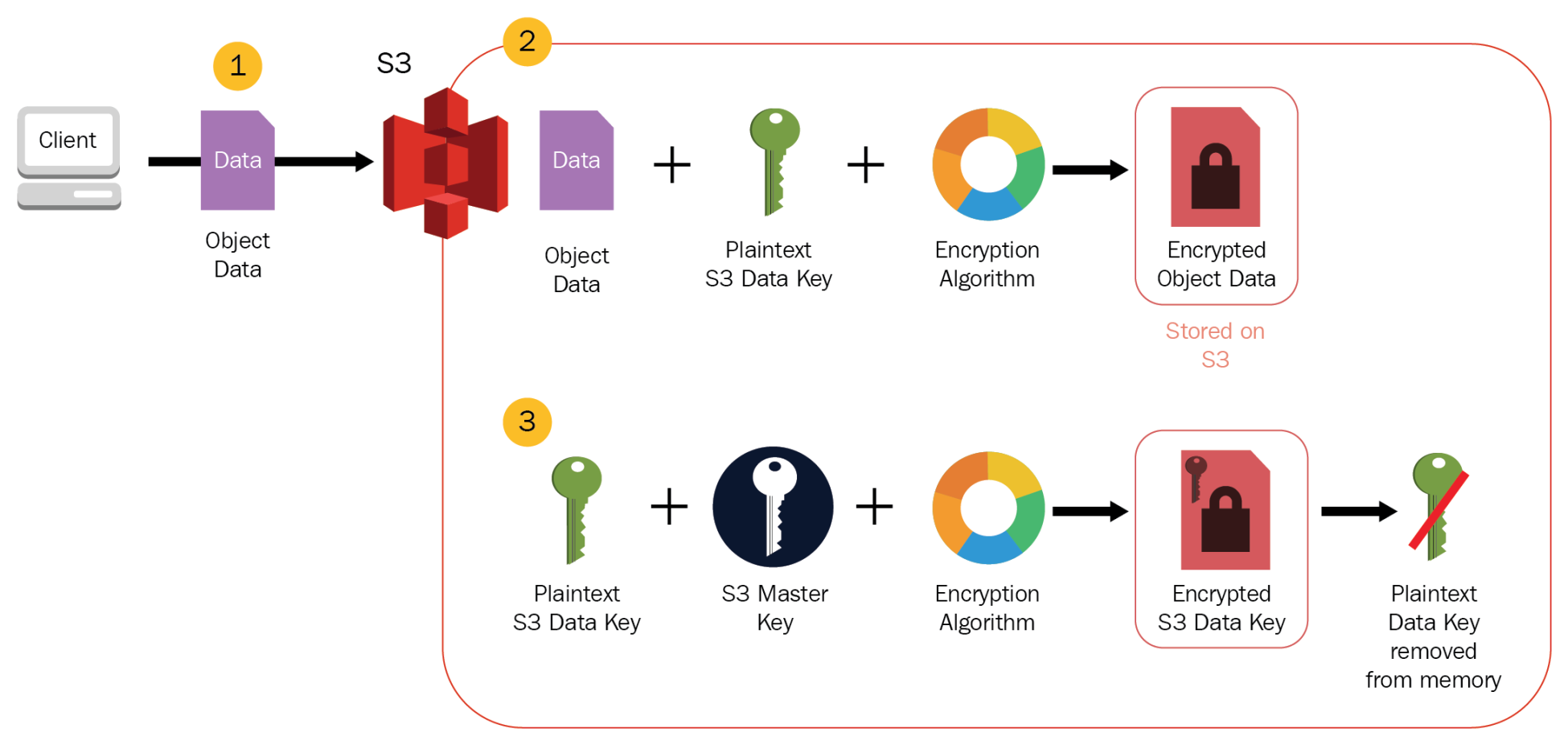
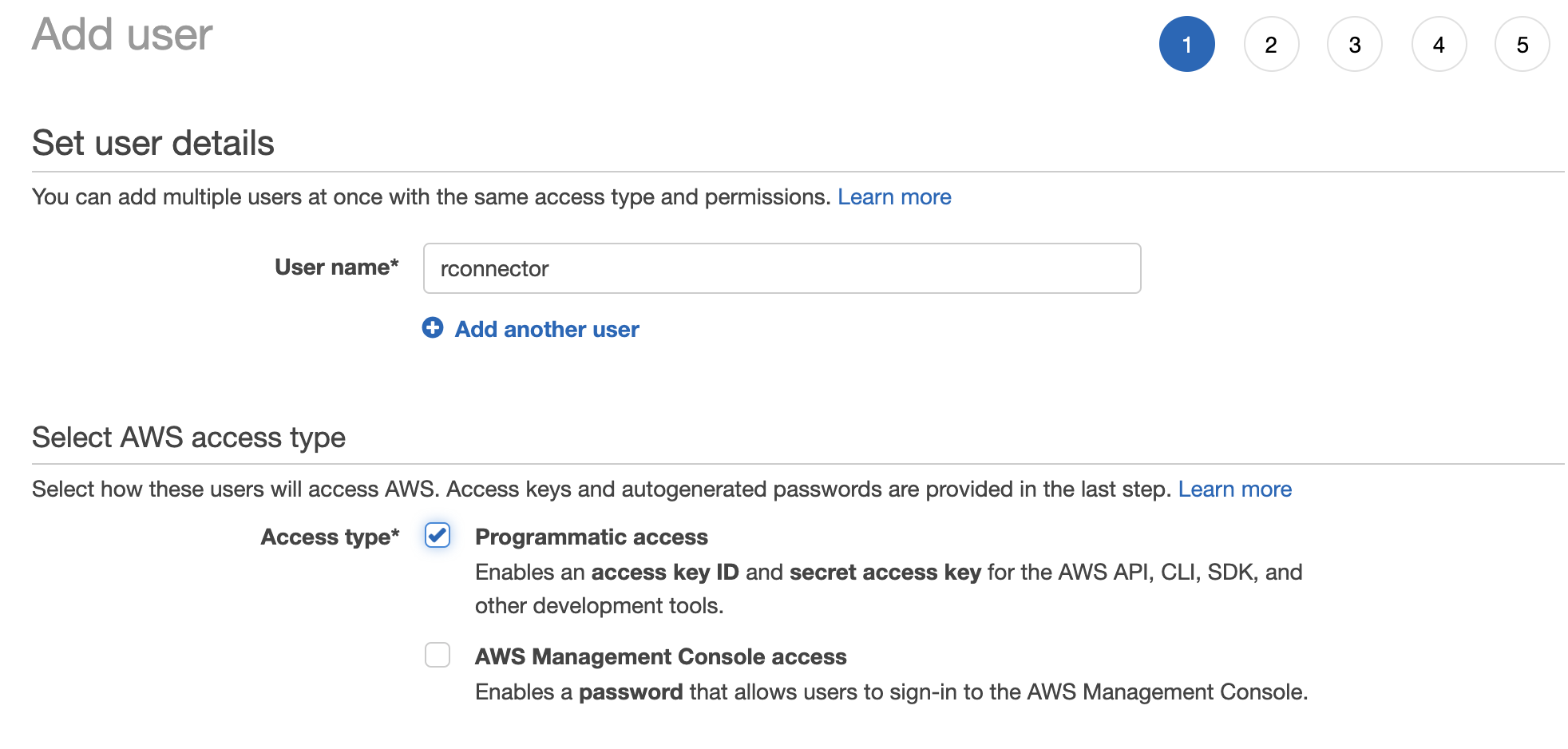
How to use KMS and IAM to enable independent security controls for encrypted data in S3 | AWS Security Blog
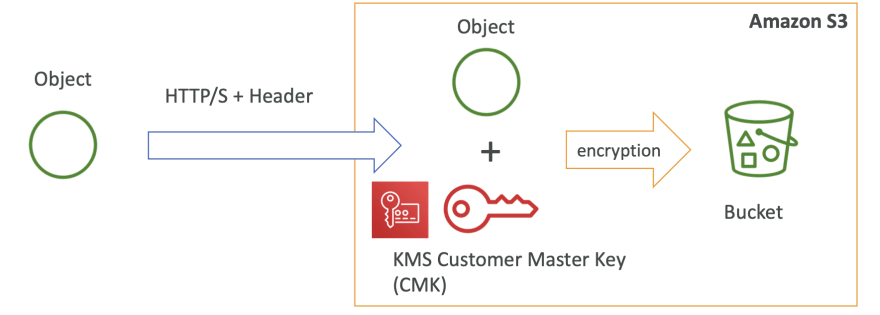
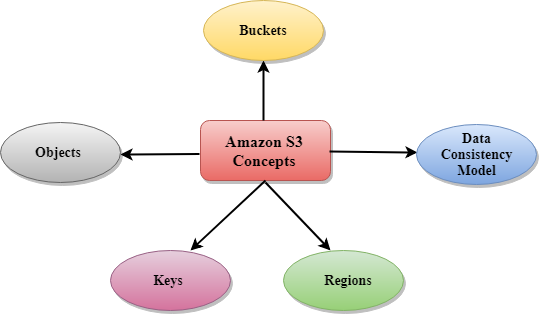
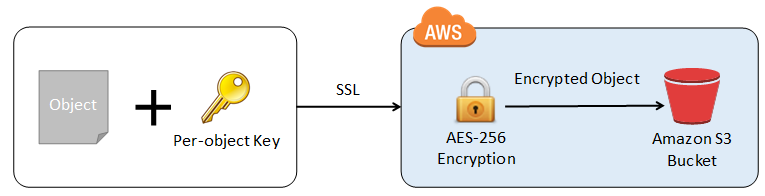
Difference between AWS S3 Bucket Encryption SSE-C , SSE-S3, SSE-KMS | by Alessandro Laurato | AWS Tip

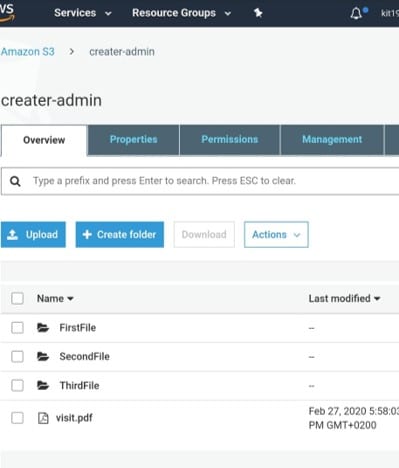
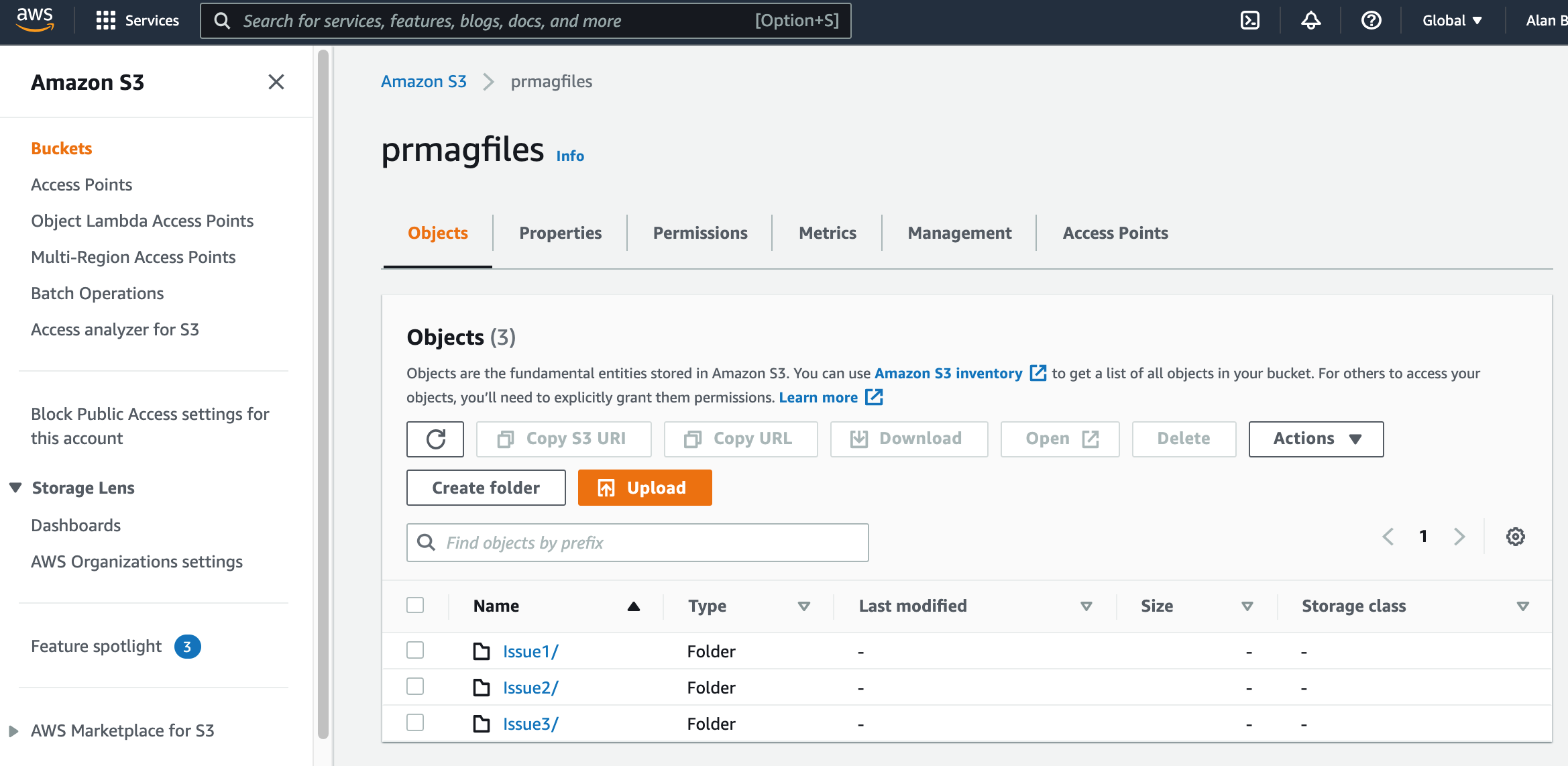
How to Use Bucket Policies and Apply Defense-in-Depth to Help Secure Your Amazon S3 Data | AWS Security Blog